In today’s cloud-driven world, securing multi-cloud environments is more critical than ever. Businesses leveraging multi-cloud setups face unique challenges that demand innovative solutions. Enter advanced Zero Trust models: a revolutionary approach to fortifying cloud-native security. This blog delves into the why, what, and how of Zero Trust in multi-cloud architectures—essential knowledge for IT professionals and enterprises.
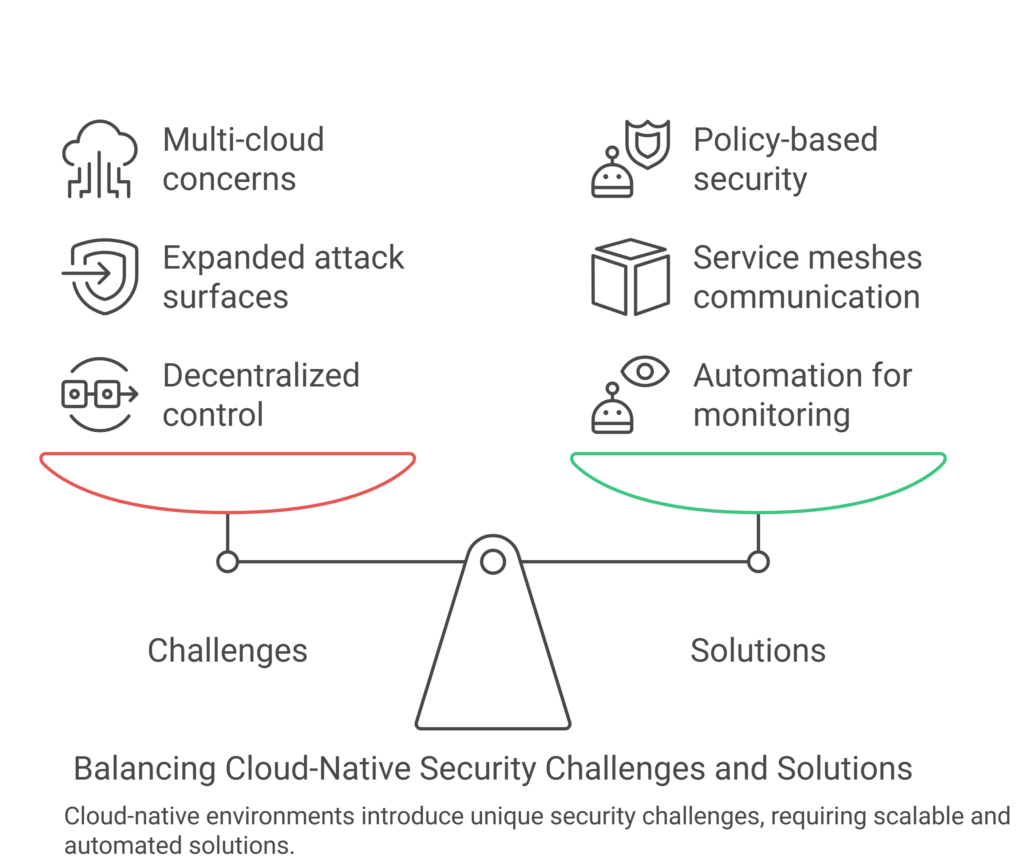
Understanding Cloud-Native Security Cloud-native security is defined by its principles of scalability, resilience, and automation. However, securing cloud-native applications presents challenges such as:
- Lack of centralized control.
- Increased attack surfaces due to distributed environments.
Adopting a robust multi-cloud security architecture ensures enterprises stay ahead of potential threats.
What is a Zero Trust Model? The Zero Trust model operates on a simple yet powerful principle: Never trust, always verify. Unlike traditional perimeter-based security, Zero Trust assumes breaches are inevitable. Here’s why it’s indispensable in securing multi-cloud environments:
- Traditional security’s limitations: Firewalls and VPNs cannot address modern attack vectors.
- Zero Trust evolution: Identity verification and real-time analytics fortify this model.
The Rise of Multi-Cloud Architectures Organizations now embrace multi-cloud setups for redundancy, flexibility, and vendor diversification. However, these benefits come with security challenges:
- Data silos between cloud providers.
- Complex access management across platforms.
Real-world example: A global enterprise using AWS, Azure, and Google Cloud can experience seamless operations yet face increased security risks without a cohesive strategy.
Advanced Zero Trust Models for Multi-Cloud Architectures Advanced Zero Trust models integrate seamlessly with multi-cloud security architecture, focusing on:
- Identity and Access Management (IAM):
- Enforce identity-based security models using MFA and adaptive authentication.
- Example code snippet for IAM policy enforcement in AWS:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::123456789012:role/example-role"
}
]
}
- Endpoint and Workload Protection:
- Use secure workload protection tools to monitor activity.
- Example: Automated container scanning for vulnerabilities using Docker:
docker scan my-container:latest –json > scan-results.json
cat scan-results.json
- Network Segmentation and Monitoring:
- Micro-segmentation isolates sensitive data.
- Example of configuring segmentation using Kubernetes:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: deny-all
spec:
podSelector:
matchLabels: {}
policyTypes:
- Ingress
- Egress
- Automation and AI:
- AI-powered analytics tools streamline anomaly detection.
- Example of setting up a basic anomaly detection pipeline in Python:
from sklearn.ensemble import IsolationForest
import numpy as np
# Sample data
data = np.array([[1, 2], [2, 3], [10, 10]])
clf = IsolationForest(random_state=42).fit(data)
anomalies = clf.predict(data)
print("Anomalies detected:", anomalies)
Implementing Zero Trust in Multi-Cloud Environments Follow these best practices to deploy Zero Trust effectively:
- Unified policy enforcement: Ensure consistent security rules across all platforms.
- Real-time monitoring: Use analytics tools like Splunk or Azure Sentinel.
- Secure DevOps pipelines: Integrate security into CI/CD workflows.
Tools like Palo Alto Prisma Cloud and HashiCorp Vault make implementation seamless.
Benefits of Zero Trust in Multi-Cloud Security Adopting advanced Zero Trust models delivers:
- Improved security posture: Minimize breach risks.
- Compliance: Simplified adherence to regulations like GDPR and HIPAA.
- Enhanced governance: Streamlined audit processes.
Challenges and Limitations of Zero Trust in Multi-Cloud While effective, Zero Trust is not without challenges:
- Complexity: Requires a deep understanding of cloud platforms.
- Balancing user experience: Overly stringent policies can hinder productivity.
- Costs: Initial setup and ongoing maintenance can be resource-intensive.
Case Studies: Successful Zero Trust Implementations
- TechCorp: Deployed IAM solutions across AWS and Azure, reducing breaches by 40%.
- FinServe: Integrated secure workload protection, enhancing compliance with PCI DSS.
Key takeaway: Tailored strategies yield the best results.
Future Trends in Cloud-Native Security and Zero Trust The future of multi-cloud security architecture is bright:
- AI and machine learning: Enhanced threat detection and response.
- Regulatory landscapes: Governments pushing for stricter compliance.
- Emerging technologies: Quantum computing’s impact on encryption.
Conclusion Advanced Zero Trust models redefine cloud-native security by addressing the complexities of securing multi-cloud environments. Enterprises must adopt these models to safeguard their digital assets and remain competitive.
Call-to-action: Ready to enhance your cloud security? Contact us at [Your Company Name], and let’s build a resilient multi-cloud security architecture together.
Meta Description Securing multi-cloud environments is no longer optional. Learn how multi-cloud security architecture and advanced Zero Trust models provide unmatched protection for your enterprise.
FAQs
- What is Zero Trust in cloud security?
Zero Trust is an identity-based security model that assumes no entity is trusted by default. It ensures maximum protection with continuous verification.
- Why is multi-cloud security important?
Multi-cloud setups face unique challenges. Securing multi-cloud environments ensures seamless operations and robust data protection.
- How does Zero Trust improve multi-cloud security?
By enforcing secure workload protection and real-time monitoring, Zero Trust models minimize vulnerabilities and lateral attack risks.
- What tools support Zero Trust implementation?
Tools like Palo Alto Prisma Cloud and Azure AD help enforce identity-based security models and manage access seamlessly.
- What challenges do enterprises face with Zero Trust?
Enterprises struggle with complexity, costs, and balancing user productivity while maintaining secure access management.
- Can AI enhance Zero Trust models?
Yes, AI enhances multi-cloud security architecture by proactively detecting threats and improving response efficiency.
- What are the benefits of a Zero Trust approach?
Improved security posture, reduced breach risks, and enhanced compliance with strict regulatory standards.
- Is Zero Trust suitable for all organizations?
Yes, any enterprise leveraging multi-cloud setups can benefit. Customizing the strategy ensures optimal performance and security.